%global _empty_manifest_terminate_build 0
Name: python-opencve
Version: 1.4.1
Release: 1
Summary: CVE Alerting Platform
License: BSD License
URL: https://github.com/opencve/opencve
Source0: https://mirrors.aliyun.com/pypi/web/packages/84/31/aac3ebf758b773f7a1c176df24235864f6708431426fdf0facb04cc645d1/opencve-1.4.1.tar.gz
BuildArch: noarch
Requires: python3-Flask
Requires: python3-Flask-Admin
Requires: python3-Flask-Assets
Requires: python3-Flask-DebugToolbar
Requires: python3-Flask-SQLAlchemy
Requires: python3-Flask-Migrate
Requires: python3-Flask-Login
Requires: python3-Flask-WTF
Requires: python3-Flask-User
Requires: python3-Flask-Gravatar
Requires: python3-Flask-Paginate
Requires: python3-Flask-RESTful
Requires: python3-Flask-Limiter
Requires: python3-SQLAlchemy
Requires: python3-SQLAlchemy-Utils
Requires: python3-psycopg2-binary
Requires: python3-Redis
Requires: python3-arrow
Requires: python3-celery
Requires: python3-cpe
Requires: python3-untangle
Requires: python3-cssmin
Requires: python3-jsmin
Requires: python3-requests
Requires: python3-nested-lookup
Requires: python3-deepdiff
Requires: python3-gunicorn
Requires: python3-vine
Requires: python3-click
Requires: python3-werkzeug
Requires: python3-itsdangerous
Requires: python3-markupSafe
Requires: python3-jinja2
Requires: python3-importlib-metadata
Requires: python3-email-validator
Requires: python3-pytest
Requires: python3-pytest-cov
Requires: python3-pytest-freezegun
Requires: python3-black
Requires: python3-beautifulsoup4
Requires: python3-Flask-Sendmail-ng
%description
Try **for free** OpenCVE on [https://www.opencve.io](https://www.opencve.io) or check [documentation](https://docs.opencve.io) to install it yourself.
## What is OpenCVE
**OpenCVE** is a platform used to locally import the list of CVEs and perform searches on it (by vendors, products, CVSS, CWE...).
Users subscribe to vendors or products, and OpenCVE alerts them when a new CVE is created or when an update is done in an existing CVE.
## Features
- **Explore** the CVE database and filter the results by Vendor, Product, CVSS score or CWE
- **Subscribe** to vendors and products extracted from CPE
- **Be notified** for new CVE and for CVE updates based on subscriptions
- **Analyse** all CVE details (vendors, products, CVSS score, CPE, CWE, References...)
- **Create** custom tags (unread, important, devteam...) to organize the CVE list
- **Display** the history of each CVE and see their last changes in the homepage
- **Retrieve** the last changes in custom reports
- **Customize** the notification settings (frequency, filter by CVSS score...)
- **Integrate** OpenCVE with your own tools using the Rest API
You can use **for free** these features on the public instance: [https://www.opencve.io](https://www.opencve.io).
## How does it work
OpenCVE uses the [JSON feed](https://nvd.nist.gov/vuln/data-feeds#JSON_FEED) provided by the [NVD](https://nvd.nist.gov/) to update the local list of CVEs.
After an initial import, a background task is regularly executed to synchronize the local copy with the NVD feed. If a new CVE is added, or if a change is detected, the subscribers of the related vendors and products are alerted.
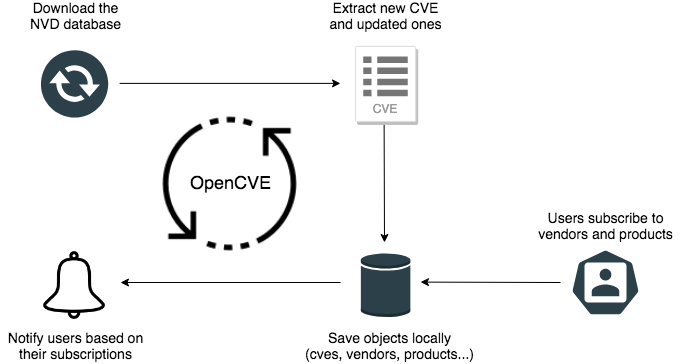
Read the [How It Works](https://docs.opencve.io/how-it-works/) guide to learn in details how OpenCVE works.
## Requirements
OpenCVE works with **Python >=3.7**.
It uses the JSONB feature for performance, so you will need a **PostgreSQL** instance to store the data (CVE, Users, Vendors, Products, Subscriptions, ...). Other engines are not supported.
The **pg_trgm** module of PostgreSQL is required to let you search in the CVEs list. The [upgrade-db](https://docs.opencve.io/commands/#upgrade-db) command will enable it for you, but you can also do it yourself if you prefer (`CREATE EXTENSION pg_trgm`). From PostgreSQL 13 this module is considered as trusted, meaning it can be installed by non-superusers with the CREATE privilege.
Celery is used to periodically fetch the NVD database and update the list of CVEs. For that you will need a broker : we recommend you **Redis** for the ease of installation. Futhermore it is possible that future versions of OpenCVE will use a cache feature, in that case the Redis requirement will already be filled for you.
During the import of initial data OpenCVE will download and parse huge files, like the CPE dictionnary. For that we recommend you **3.5G RAM** at least.
## Installation
We provide 2 methods to install OpenCVE :
- [manual installation](https://docs.opencve.io/installation/manual/)
- [docker installation](https://docs.opencve.io/installation/docker/)
The second method can be useful if you don't want to manage the dependencies (like PostgreSQL, Redis or Celery).
Check these documentations for the details of each step (initial import, admin creation, etc).
%package -n python3-opencve
Summary: CVE Alerting Platform
Provides: python-opencve
BuildRequires: python3-devel
BuildRequires: python3-setuptools
BuildRequires: python3-pip
%description -n python3-opencve
Try **for free** OpenCVE on [https://www.opencve.io](https://www.opencve.io) or check [documentation](https://docs.opencve.io) to install it yourself.
## What is OpenCVE
**OpenCVE** is a platform used to locally import the list of CVEs and perform searches on it (by vendors, products, CVSS, CWE...).
Users subscribe to vendors or products, and OpenCVE alerts them when a new CVE is created or when an update is done in an existing CVE.
## Features
- **Explore** the CVE database and filter the results by Vendor, Product, CVSS score or CWE
- **Subscribe** to vendors and products extracted from CPE
- **Be notified** for new CVE and for CVE updates based on subscriptions
- **Analyse** all CVE details (vendors, products, CVSS score, CPE, CWE, References...)
- **Create** custom tags (unread, important, devteam...) to organize the CVE list
- **Display** the history of each CVE and see their last changes in the homepage
- **Retrieve** the last changes in custom reports
- **Customize** the notification settings (frequency, filter by CVSS score...)
- **Integrate** OpenCVE with your own tools using the Rest API
You can use **for free** these features on the public instance: [https://www.opencve.io](https://www.opencve.io).
## How does it work
OpenCVE uses the [JSON feed](https://nvd.nist.gov/vuln/data-feeds#JSON_FEED) provided by the [NVD](https://nvd.nist.gov/) to update the local list of CVEs.
After an initial import, a background task is regularly executed to synchronize the local copy with the NVD feed. If a new CVE is added, or if a change is detected, the subscribers of the related vendors and products are alerted.

Read the [How It Works](https://docs.opencve.io/how-it-works/) guide to learn in details how OpenCVE works.
## Requirements
OpenCVE works with **Python >=3.7**.
It uses the JSONB feature for performance, so you will need a **PostgreSQL** instance to store the data (CVE, Users, Vendors, Products, Subscriptions, ...). Other engines are not supported.
The **pg_trgm** module of PostgreSQL is required to let you search in the CVEs list. The [upgrade-db](https://docs.opencve.io/commands/#upgrade-db) command will enable it for you, but you can also do it yourself if you prefer (`CREATE EXTENSION pg_trgm`). From PostgreSQL 13 this module is considered as trusted, meaning it can be installed by non-superusers with the CREATE privilege.
Celery is used to periodically fetch the NVD database and update the list of CVEs. For that you will need a broker : we recommend you **Redis** for the ease of installation. Futhermore it is possible that future versions of OpenCVE will use a cache feature, in that case the Redis requirement will already be filled for you.
During the import of initial data OpenCVE will download and parse huge files, like the CPE dictionnary. For that we recommend you **3.5G RAM** at least.
## Installation
We provide 2 methods to install OpenCVE :
- [manual installation](https://docs.opencve.io/installation/manual/)
- [docker installation](https://docs.opencve.io/installation/docker/)
The second method can be useful if you don't want to manage the dependencies (like PostgreSQL, Redis or Celery).
Check these documentations for the details of each step (initial import, admin creation, etc).
%package help
Summary: Development documents and examples for opencve
Provides: python3-opencve-doc
%description help
Try **for free** OpenCVE on [https://www.opencve.io](https://www.opencve.io) or check [documentation](https://docs.opencve.io) to install it yourself.
## What is OpenCVE
**OpenCVE** is a platform used to locally import the list of CVEs and perform searches on it (by vendors, products, CVSS, CWE...).
Users subscribe to vendors or products, and OpenCVE alerts them when a new CVE is created or when an update is done in an existing CVE.
## Features
- **Explore** the CVE database and filter the results by Vendor, Product, CVSS score or CWE
- **Subscribe** to vendors and products extracted from CPE
- **Be notified** for new CVE and for CVE updates based on subscriptions
- **Analyse** all CVE details (vendors, products, CVSS score, CPE, CWE, References...)
- **Create** custom tags (unread, important, devteam...) to organize the CVE list
- **Display** the history of each CVE and see their last changes in the homepage
- **Retrieve** the last changes in custom reports
- **Customize** the notification settings (frequency, filter by CVSS score...)
- **Integrate** OpenCVE with your own tools using the Rest API
You can use **for free** these features on the public instance: [https://www.opencve.io](https://www.opencve.io).
## How does it work
OpenCVE uses the [JSON feed](https://nvd.nist.gov/vuln/data-feeds#JSON_FEED) provided by the [NVD](https://nvd.nist.gov/) to update the local list of CVEs.
After an initial import, a background task is regularly executed to synchronize the local copy with the NVD feed. If a new CVE is added, or if a change is detected, the subscribers of the related vendors and products are alerted.

Read the [How It Works](https://docs.opencve.io/how-it-works/) guide to learn in details how OpenCVE works.
## Requirements
OpenCVE works with **Python >=3.7**.
It uses the JSONB feature for performance, so you will need a **PostgreSQL** instance to store the data (CVE, Users, Vendors, Products, Subscriptions, ...). Other engines are not supported.
The **pg_trgm** module of PostgreSQL is required to let you search in the CVEs list. The [upgrade-db](https://docs.opencve.io/commands/#upgrade-db) command will enable it for you, but you can also do it yourself if you prefer (`CREATE EXTENSION pg_trgm`). From PostgreSQL 13 this module is considered as trusted, meaning it can be installed by non-superusers with the CREATE privilege.
Celery is used to periodically fetch the NVD database and update the list of CVEs. For that you will need a broker : we recommend you **Redis** for the ease of installation. Futhermore it is possible that future versions of OpenCVE will use a cache feature, in that case the Redis requirement will already be filled for you.
During the import of initial data OpenCVE will download and parse huge files, like the CPE dictionnary. For that we recommend you **3.5G RAM** at least.
## Installation
We provide 2 methods to install OpenCVE :
- [manual installation](https://docs.opencve.io/installation/manual/)
- [docker installation](https://docs.opencve.io/installation/docker/)
The second method can be useful if you don't want to manage the dependencies (like PostgreSQL, Redis or Celery).
Check these documentations for the details of each step (initial import, admin creation, etc).
%prep
%autosetup -n opencve-1.4.1
%build
%py3_build
%install
%py3_install
install -d -m755 %{buildroot}/%{_pkgdocdir}
if [ -d doc ]; then cp -arf doc %{buildroot}/%{_pkgdocdir}; fi
if [ -d docs ]; then cp -arf docs %{buildroot}/%{_pkgdocdir}; fi
if [ -d example ]; then cp -arf example %{buildroot}/%{_pkgdocdir}; fi
if [ -d examples ]; then cp -arf examples %{buildroot}/%{_pkgdocdir}; fi
pushd %{buildroot}
if [ -d usr/lib ]; then
find usr/lib -type f -printf "\"/%h/%f\"\n" >> filelist.lst
fi
if [ -d usr/lib64 ]; then
find usr/lib64 -type f -printf "\"/%h/%f\"\n" >> filelist.lst
fi
if [ -d usr/bin ]; then
find usr/bin -type f -printf "\"/%h/%f\"\n" >> filelist.lst
fi
if [ -d usr/sbin ]; then
find usr/sbin -type f -printf "\"/%h/%f\"\n" >> filelist.lst
fi
touch doclist.lst
if [ -d usr/share/man ]; then
find usr/share/man -type f -printf "\"/%h/%f.gz\"\n" >> doclist.lst
fi
popd
mv %{buildroot}/filelist.lst .
mv %{buildroot}/doclist.lst .
%files -n python3-opencve -f filelist.lst
%dir %{python3_sitelib}/*
%files help -f doclist.lst
%{_docdir}/*
%changelog
* Thu Jun 08 2023 Python_Bot - 1.4.1-1
- Package Spec generated



